Zero-Byte PNG Steals 1TB of Secrets — While 37 Governments Still Use WinRAR: A Global Cyber Farce
TL;DR
- State-Sponsored Threat Group 'Shadow Campaigns' Compromised 70+ Government Entities Across 37 Countries
- Google Complies with ICE Subpoena Demanding Data on Student Activist Amandla Thomas-Johnson
🤯 1TB Stolen via Zero-Byte PNG: Shadow Campaigns Breaches 37 Nations Using CVEs Even Patched in 2019
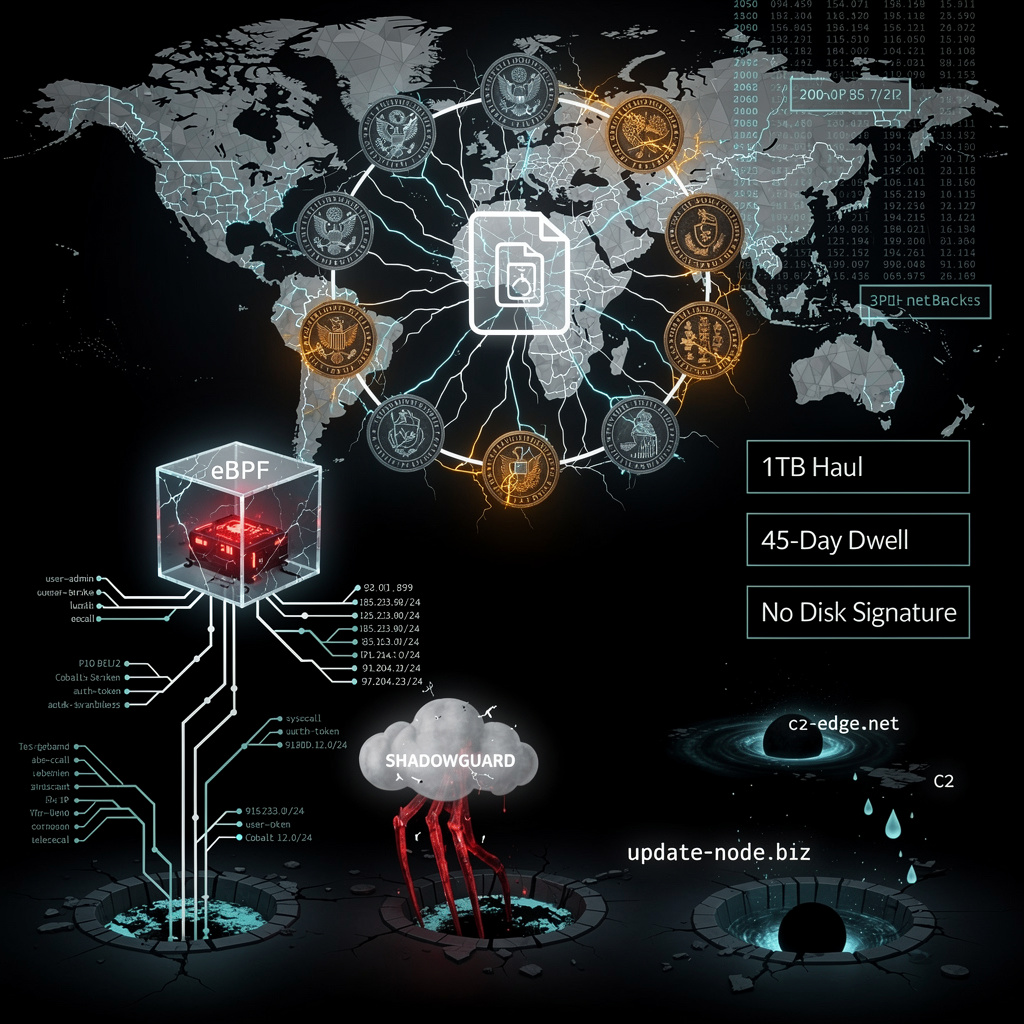
200+ malicious IPs. 1TB of diplomatic secrets stolen. And the hackers? They hid in a ZERO-BYTE PNG. 🤯 ShadowGuard’s eBPF rootkit doesn’t just bypass antivirus—it rewrites the OS to pretend nothing’s wrong. Meanwhile, 37 governments still use WinRAR in 2026. 🤡 Brazil’s mines. Honduras’ elections. Taiwan’s telecoms. All pwned. Who’s paying for this? Your tax dollars—or your next power outage?
“Shadow Campaigns” just turned 37 foreign ministries into unpaid interns—clicking phishing links, blessing unsigned DLLs, and cheerfully piping trade secrets straight to AS 9808. The haul: 1 TB of budget spreadsheets, energy contracts, and who-knows-what embassy gossip, all compressed through Cloudflare so it arrives faster than your expense report.
How Did a Zero-Byte PNG Outrank Entire CERT Teams?
Simple math: one fake staff-reorg email + one Cobalt Strike beacon = kernel-level ShadowGuard. The eBPF module hijacks syscalls, hides its own PID, and lets Mimikatz run a 24-hour credential buffet. CVE-2019-11580 and a fresh WinRAR bug (CVE-2025-8088) handle privilege escalation—because nothing says “state-funded” like recycling four-year-old flaws still sitting in patch limbo.
Where’s the 30-Percent Detection Discount?
Seventy breached agencies, yet 45-day dwell times on 30 % of networks. Reason: ShadowGuard’s bytecode signature never hits disk, so your grandfather’s IOC list is just a souvenir. If your EDR can’t see its own syscalls being mugged, you’re not “monitoring,” you’re journaling your own obituary.
Can We Patch Our Way Out of This?
Only if you enjoy Sisyphus cosplay. Block the 200-IP netblock, sinkhole the C2 domains, and YARA-hunt the Diaoyu loader—then watch TGR-STA-1030 swap to file-less SparkRat and abuse the next SAP N-day. Real fix: eBPF-aware EDR, MFA everywhere, and segment ministry VLANs like they’re radioactive. Anything less is just leaving the key under a diplomatic pouch.
Will the Next Invoicing Cycle Include Deepfake Ministers?
Mid-term forecast: supply-chain poison of open-source libs, AI-generated phishing lures, and Linux-powered SCADA rootkits. Translation—they’ll invoice you for the breach, then speak at your conference about resilience. Start pricing kernel-integrity monitoring now; by Q3 the same actors will be billing in Bitcoin for not turning your grid into a lava lamp.
🚨 Google Delivers Bank Accounts to ICE: 28,622 Subpoenas, Zero Warrants — Activist in Senegal Targeted
Google handed ICE 28,622 user records in Q1 2025 — including bank accounts, credit cards, and IP logs — just 2 minutes after a student’s visa got revoked. 🚨 No warrant. No judge. Just a subpoena and a corporate shrug. Amandla Thomas-Johnson, now in Senegal, didn’t even know his financial data was sold to border enforcers. 🇸🇳💸 Should tech giants be ICE’s data janitors — or should they stop cleaning up human rights violations for free?
Another Wednesday, another fresh hell in the cloud: Google coughed up Amandla Thomas-Johnson’s entire digital life—bank digits, phone digits, IP digits, probably the digits he used to pick the lock on his dorm—because ICE mailed over an “administrative subpoena,” the legal equivalent of a Post-it note that says “gimme.” No judge, no warrant, no problem.
🧾 How Thin Is the Paper Shield?
- Statute: 8 U.S.C. § 1225(d) – lets ICE self-issue data demands.
- Review required: Zero.
- Data handed over: Everything except maybe his cafeteria punch card.
- Timeline: Two-minute window after Cornell yanked the visa—faster than most people microwave popcorn.
📈 The Subpoena Scoreboard (Because Metrics Matter)
Google fielded 28,622 U.S. subpoenas in Q1 2025, up 15 % year-over-year. That’s one every 92 seconds—a growth rate most startups would kill for.
🎯 Pattern Recognition for the Paranoid
- Target profile: Student activists, immigration critics, pro-Palestinian posters.
- Data scope: Cross-service identifiers—IP, device ID, credit-card, bank account.
- Geography: U.S. agency reaches into Senegal & Switzerland without leaving the couch.
- Pushback: EFF + ACLU sent strongly-worded PDFs; ICE shrugged.
⚖️ Risk-Benefit, Minus the Kool-Aid
Privacy risk: Identity-theft Christmas list now lives in DHS servers.
Legal exposure: SCA § 2703 says “electronic communications” get robes-and-wigs review—never happened.
Chilling effect: If you tweet about ICE raids, congratulations, your bank balance is now part of the case file.
Operational benefit to ICE: One-stop shopping for deportation evidence.
Reputational hit to Google: Users discover “Don’t be evil” came with an asterisk and a fax number for subpoenas.
🔧 Four Lines of Code-Flavored Defense
- Auto-strip financial data unless a court order shows up—because money talks, subpoenas shouldn’t.
- Split admin vs. judicial metrics in transparency reports—sunlight is free, unlike lawyer hours.
- 48-hour user heads-up (where gag orders don’t gag) so targets can lawyer-up before the data ships.
- Amicus brief cannon—lobby to force warrants for any request touching protected speech; make Congress feel the bandwidth burn.
🔮 Short-Term Forecast
Expect lawsuits by lunchtime, a congressional hearing by summer, and zero changes by Christmas—unless the subpoena count starts costing stock price. Until then, keep your activism on paper and your bank account under the mattress.
In Other News
- AMD AutoUpdate Software Unpatched for RCE Vulnerability, Report Closed as 'Wont Fix'
Comments ()