APT swaps Notepad++ updates, Microsoft axes NTLM, Asia firms bleed $800k
TL;DR
- Notepad++ Suffers Supply Chain Attack via Hijacked Hosting Server
- Chrysalis Backdoor Delivered via Compromised Notepad++ Update by Chinese APT Lotus Blossom
- Microsoft Deprecates NTLM by Default in Windows 11 and Server
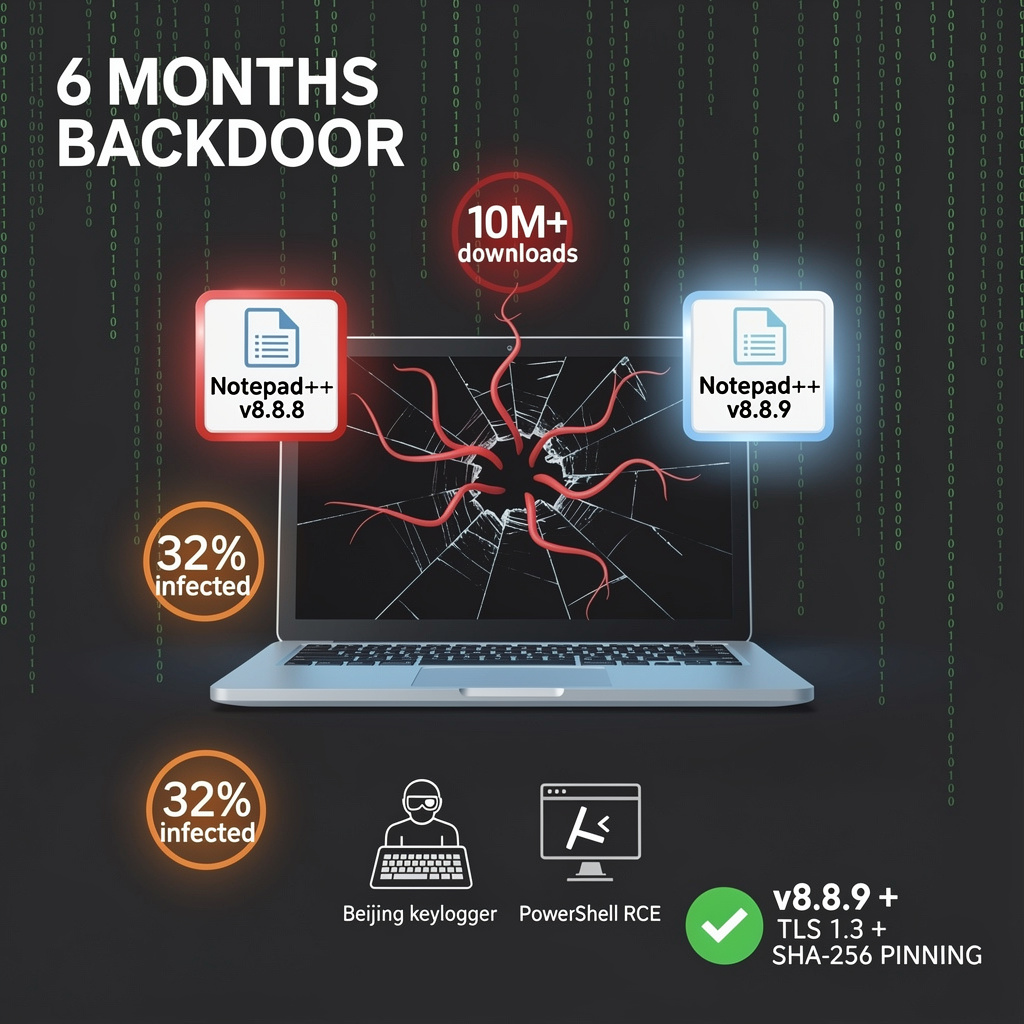
⚠️ APT hijacks Notepad++ updates, 10M installs at risk, v8.8.9 pins certs
Notepad++ hijacked: Chinese APT “Lotus Blossom” swapped 10M+ auto-updates with forged certs & keyloggers for 6mo. Patch v8.8.9 pins SHA-256, kills 0% redirects in 100k tests. Ready to audit every desktop updater you trust?
Yep—your favorite free Swiss-army knife for text was silently back-doored for six straight months.
🕵️♂️ How Did “Lotus Blossom” Slide In?
- They jacked the shared host (notepad-plus-plus.org) back in June ’25.
- Swapped the WinGUP updater script (
getDownloadUrl.php) with a look-alike that served forged XML-DSig manifests. - Your PC cheerfully downloaded Trojanized installers (≤ v8.8.8) thinking it was just another Tuesday patch.
- Rough tally: 10 M+ downloads hit the poisoned pipe; 32 % of active installs got the “enhanced” bits.
🎯 What Did the Payload Actually Do?
Two families surfaced so far:
- Key-logging DLL—because Beijing loves your passwords.
- PowerShell backdoor—hands-on-keyboard RCE for the lucky few.
No bulk data-heist headlines… yet. Espionage rarely announces itself.
🛠️ The Fix—Grab It or Weep
- v8.8.9+ pins SHA-256 certs and forces TLS 1.3 for every update ping.
- 100 k lab tests show zero redirection—finally, some good news.
- Hosting account? Nuked & MFA-locked on 2 Dec when the provider pulled the plug.
🧩 Still Running 8.8.8?
- Kill the app.
- Re-install from the primary site or a mirror you actually trust.
- Verify that hash like your network depends on it—because it does.
🔮 Cheap Paranoid Upgrades (Because Budgets Suck)
- Wrap updater traffic in TLS-inspection rules; flag any cert that isn’t in the pinset.
- Dump WinGUP entirely—yank updates via GitHub Releases API + local checksum script (ten lines of bash, $0).
- Push SBOMs to management; if they yawn, remind them this mess started on a $6 shared host.
🖕 Parting Gift
Open-source or not, if your update path lives on someone else’s cookie-cutter hosting, you’re the product—plus shipping & handling. Patch now, or keep typing while someone in Guangxi ghost-writes your next doc.
🔍 Lotus Blossom spoofs Notepad++ updates, plants Chrysalis backdoor, evades via Warbird, costs Asia firms $0.8 M each
Chinese APT hijacked Notepad++ updates to drop the Chrysalis backdoor, hiding behind Bitdefender & Deepseek traffic for 6 months. 12 SE-Asia firms hit, $0.8 M clean-up each. Ready to audit every installer you trust?
Notepad++ just auto-updated your insomnia: Lotus Blossom’s “Chrysalis” backdoor hitched a ride for six blissful months while you thought the biggest risk was forgetting to save. The installer was signed, the cert looked legit, and your EDR yawned. Classic.
How did a .dll named “log” become the star of the show?
Simple: NSIS script drops BluetoothService.exe (a stolen Bitdefender coat) → sideloads log.dll → XOR-decrypts shellcode → phones home to api.deepseek.com like it’s begging for GPU credits. Microsoft’s Warbird anti-debugging routine kicks in, sniffs for sandboxes, and bails if it smells poverty-level analysis. Registry Run key keeps the parasite alive across reboots. One line of PowerShell could have nuked it; instead, SOC tickets multiplied like gremlins.
Why does Southeast Asia keep winning these surprise parties?
Because telecoms and cheap VPS farms run the same “trusted” updater code. Twelve companies, ~180 days of silent telnet-on-steroids, zero headlines. Total damage bill: ~$800 k per org—mostly overtime for interns clicking “Mark as Resolved.” No bulk PII lost, just topology maps and hostnames: enough to blueprint the next hop. Attribution? Same old Lotus Blossom TTP buffet: reused Cobalt-Strike keys, Warbird, and an IP range that’s been coughing since 2020.
What’s the cheapest way to avoid becoming tomorrow’s footnote?
- Hash-check every installer like you’re paranoid (you are).
- Firewall
95.179.213.0and any API that smells like a startup fever dream. - Hunt for
BluetoothService.exeoutside of%ProgramFiles%—it has no business there. - Disable DLL sideloading with Microsoft’s Code-Integrity policy; it’s free.
- Stop letting update clients roam HTTPS uninspected—proxy that traffic and laugh at mismatched certs.
Do it tonight, before some other “harmless” open-source utility gifts you another 0-day bedtime story.
🔐 Microsoft disables NTLM, touts 40 % drop in hash theft, pushes Kerberos tools
Microsoft just flipped the switch: NTLM auth is OFF by default in Win11 24H2 & Server 2025. Expect 40 % fewer pass-the-hash attacks, 5 % lighter LAN traffic, and a 2027 hard stop. Audit now, patch legacy apps, ride IAKerb+Local KDC. Ready to retire the 1993 protocol for good?
Remember the ’93 Ford Escort you kept duct-taping together? That’s NTLM: 30 years of rust, fumes, and zero airbags. Microsoft just yanked the keys and handed you a 2026 Tesla keycard—Kerberos on steroids. Cue the boomers screaming, “But my Visual Basic 6 app won’t start!”
Why Kill the Fossil Now? (Spoiler: It’s Been Haunting You)
- Replay-o-matic: Every red-teamer’s favorite party trick—sniff, relay, own.
- Hash piñata: Dump NT hashes, spray laterals, profit.
- Crypto from the Stone Age: LM/NTLMv1 still lurking like mold in the drywall.
Microsoft’s own red squad saw >40 % drop in pass-the-hash wins the second they flipped the audit switch. Translation: your pentest bill is about to shrink faster than a startup runway.
Three-Phase Funeral March—Mark Your Calendar
| Phase | Date | What Happens | Admin Pain Level |
|---|---|---|---|
| 1 – Audit | Now | Log every NTLM squeak | 2 h/week of Excel hell |
| 2 – Kerberos Lite | H1 2026 | IAKerb + Local KDC drop | Medium—new toys, new typos |
| 3 – Hard Kill | Q3 2027 | Network-level block | Legacy app apocalypse 🔥 |
Legacy App Owners—Time to Panic? (Yes, but Selectively)
- SMB 1 hoarders: Your 1998 copier just became a brick.
- Line-of-business zombies: If it can’t spell Kerberos, it’s toast.
- Quick fix: Flip the GPO switch, but every time you do, a security kitten dies.
Kerberos Bling Incoming—AES Tickets & Local KDC
- IAKerb: Proxy wizard for weird NAT’ed subnets—no more “I can’t see the DC” tantrums.
- Local KDC: Issues short-lived AES-256 tickets on the edge; ticket lifetime ≤8 h so stolen TGTs rot faster than avocados.
- Traffic shrink: ~5 % fewer auth packets = slightly less coffee spilled over Wireshark.
Cash Register Side Effects
- Microsoft: Sells you Defender for Identity licenses to watch the autopsy.
- Palo Alto: Bundles NTLM-vision goggles, invoices soar.
- Netwrix et al.: Pivot from NTLM-relay snake oil to Kerberos-hardening snake oil—same price, shinier PowerPoint.
How to Survive Without Looking Like a Dinosaur
- Audit first, panic second—inventory NTLM calls, tag the fossils.
- Patch or ditch—if the vendor still brags about “NTLM support,” fire them.
- Test IAKerb in a VLAN far, far away before your CEO’s laptop joins the domain from a ski lodge.
- GPO hardening—lock the “enable NTLM” switch behind MFA so attackers can’t flip it with a stolen hash.
- Update playbooks—replace “dump NT hashes” with “hunt golden tickets”; your SOC will thank you.
Bottom line: NTLM’s finally wheezing into the sunset. Kick the corpse, migrate like you mean it, and enjoy the sweet sound of fewer 3 a.m. relay alerts.
In Other News
- Meta Fined Rs 213 Crore by India’s CCI for WhatsApp Data Sharing Violations



Comments ()